Advertisement
- Don't Miss:
- 8 free Wi-Fi stumbling and surveying tools for Windows and Mac
- The 10 most powerful companies in enterprise networking 2020
- How microsegmentation architectures differ
- What is SASE? A cloud service that marries SD-WAN with security
- 8 free Wi-Fi stumbling and surveying tools for Windows and Mac

Searching Wikipedia on the Linux command line with wikit
Wikit is a clever command for running Wikipedia searches from the Linux command line. It can help you run searches and save the output in text files. Take a look at how easily it works and learn what you need to know to get the...

Microsoft updates Azure Stack HCI
With VMware and Nutanix pretty much owning the market, Microsoft is playing catch up.
![Access control setting on a virtual display [authentication/privileges]](https://images.idgesg.net/images/article/2020/07/access_control_setting_on_virtual_display_authentication_privileges_by_putilich_gettyimages-1215246629_cso_nw_2400x1600-100852996-medium.3x2.jpg)
How to deploy 802.1x for Wi-Fi using WPA3-Enterprise
Wi-Fi Protected Access 3 can provide authentication with enhanced security.
Advertisement

SolarWinds roundup: Fixes, new bad actors, and what the company knew
A roundup of events from what is emerging as the biggest security breech ever.

SASE check list: 7 key evaluation criteria
Not all SASE providers are created equal, and here's how IT decision makers can examine their options and choose the best fit.
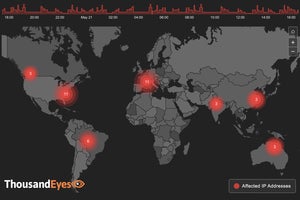
Weekly internet health check, US and worldwide
ThousandEyes, which tracks internet and cloud traffic, provides Network World with weekly updates on the performance of three categories of service provider: ISP, cloud provider, UCaaS

Deloitte: 5G to drive edge, open RAN to the forefront in 2021
5G cellular wireless, edge computing technology face a year of growth

Using the Linux arping command to ping local systems
arp命令可以ping本地系统out whether they are responsive, and with the help of scripts, can ping specific IP-address ranges.

Cisco takes additional steps to fight counterfeit network gear
Cisco has added new security labels and enhanced cooperation with online marketplaces to crack down on criminals hawking counterfeit network hardware and software.

Lenovo unveils hybrid-cloud management tools
The new solutions are designed to enable businesses to harness data more securely and efficiently, from edge to core to cloud.
-
White Paper
-
-
-
Advertisement

SolarWinds Trojan: Affected enterprises must use hot patches, isolate compromised gear
SolarWinds is recommending that customers hit by the Trojan embedded in a version of its Orion network-monitoring platform update to a new release of the software as Microsoft, Cisco, others weigh in.

Trojan in SolarWinds security has far-reaching impact
有许多专业t agencies and almost all of the Fortune 500 as customers, the SolarWinds breach is very wide-ranging and very dangerous.

SolarWinds attack explained: And why it was so hard to detect
A group believed to be Russia's Cozy Bear gained access to government and other systems through a compromised update to SolarWinds' Orion software. Most organizations aren't prepared for this sort of software supply chain attack.

Creating your own cowsay messenger
Want to add a personal image or company logo for using with cowsay? It's easier than you might think to become a cowsay Picasso.

Tech Resume Library: 22 downloadable templates for IT pros
A well-crafted resume will attract recruiters, HR pros and hiring managers, but getting it just right is a daunting task. To jump start the process, Insider Pro has assembled this collection of real resumes revamped by professional...
From Our Advertisers
- Featured Sponsor IntelCompetitive Advantage with a Modern Data Center that Delivers Boundless Agility
- Sponsored by FortinetImplementing Security on All Edges
- Sponsored by Silver PeakSD-WAN growth drives the adoption of SD-Branch deployments
- Sponsored by HuaweiWhy transformation in energy is powered by digital











